Modern access control systems are a proactive defense
Our last Insights post introduced and outlined how modern access control increases efficiency through convenience. This post takes a deeper look at how commercial building access control systems function and protect your business. In today’s market landscape, robust security is essential to protect against an unprecedented range of threats, both malicious and accidental. While cyber security often gets the spotlight, securing the physical footprint of your organization is equally important. Modern commercial access control systems play a pivotal role in a comprehensive security strategy. They protect assets and personnel using both installed hardware and integrated software. These systems not only control who accesses specific areas but also offer advanced, flexible solutions that go beyond security. Professionally integrated systems help address corporate security concerns such as helping ensure compliance with safety regulations. They also enable real-time monitoring and facilitate rapid responses to potential threats.
How hardware enables a resilient foundation for your security
Commercial building access control systems consist of interconnected hardware devices that manage interactions at physical access points. (Some examples are door locks, card readers, and gate operators.) These tie into an electronic controller, which in turn connects to centralized software. These components work together seamlessly to enable secure access. With them, an employee could use their mobile phone as a keycard to enter their office. Similarly, a nurse can scan a keycard to admit a patient into a secure wing. Meanwhile, they allow an administrator to use the centralized software to manage and monitor all connected devices and recorded events.
ESI Technologies has extensive experience with a wide range of access control components beyond standard personnel doors. Our hands-on experience includes ADA controls, gate hardware, overhead doors, elevators, intercom stations, smart lockers, managed key systems. We also have expertise integrating other low voltage controls. When carefully selected and properly integrated, these devices meet a wide range of requirements. Their effectiveness comes from diverse hardware options and flexible, configurable functionality. Our expertise guides a path through the extensive options to solve the specific needs of your organization.
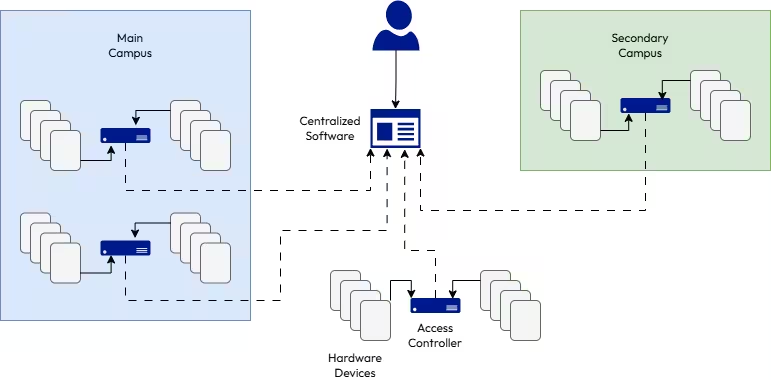
Transcend your basic lock and key
While the physical components are crucial, the real power of commercial building access control systems lie in the software controlling it all. The primary role of the software is to manage keycard validation and access control. It continuously verifies keycards (or other access identifiers) and grants temporary access to the corresponding resource. Any sort of access control, from the password on your computer to the code for your garage door, inherently verifies who an operator is and if they are allowed to perform a given action. Many systems combine these concepts—for traditional locks, a specific key is tied to the ability to perform a specific action.
Modern access control helps organizations make smarter decisions about physical security. It does this by separating identity verification (authentication) from access permission (authorization). When a user scans a keycard, the connected controller identifies the user associated with it—this is the authentication process. Next, the system checks rules to determine whether the user is authorized to access a resource or perform an action—the authorization. These rules may consider assigned access groups, time-based controls, or other integrations. Multi-factor controls, such as PIN codes, mobile devices, or biometric verification, can also be used to strengthen authentication. All of this centralized software configuration provides greater control over cardholder access.
Separating authentication and authorization also greatly enhances accountability. Since the system associates every card with a user, the control software tracks whose card initiated any event, whether authorized or unauthorized. This audit trail supports business operations, such as verifying arrival times, and helps meet oversight or legal requirements. Logging access events even help proactively solve problems that you otherwise may not be aware of—such as addressing why an employee consistently tries to enter restricted areas or who always leaves the back door propped open.
Smart software unlocks organizational efficiencies
Centralized access control software goes beyond the basics of authentication, authorization, and accountability. It also enables operational efficiencies through the programmable configuration of hardware, cardholders, and automated actions. These programmable features allow for the efficient management of cardholders, notifications of high-priority alerts, advanced customizations via software integrations, and ability to integrate access control as a component of a comprehensive security package. ESI Technology helps both with initial configuration and training as well as being available for ongoing support of advanced capabilities.
Cardholders are managed efficiently through two levels of control: as individuals and groups. At the individual level, managing the cards and details of a specific cardholder is what allows administrators to identify cards that have been lost or stolen and need disabled. Group-based access control offers a balance between ease of initial configuration and ongoing management. Policies are defined for groups—such as business roles, departments, or building tenants—and apply to all cardholders in the group. This reduces manual errors and simplifies updates to authorized cardholders or to access granted for a cardholder group.
Going beyond the audit trail that logs all events, access control systems also enable proactive security through configurable alerts. These alerts notify configured administrative users or control other events such as locking down areas or connecting to recorded video. This proactive approach allows you to respond to critical events in an appropriate and timely manner.
Integrations extend access control
The centralized access control software can be thought of as the brain of a connected network of inputs and outputs. It is able to utilize a variety of input events to trigger other actions through either integrated hardware as outputs or just in the software plane itself. An experienced integrator utilizes these programmable triggers to address a wide range of business cases, especially through integrating the card access system with other systems or hardware controls. For example, a single reader could unlock multiple doors or a crisis event could cause the lockdown of a series of doors. Depending on the installed system devices, access control systems integrate with other building systems including intercom stations, surveillance, fire detection, av, intrusion detection, hvac, lighting, or almost any low-voltage control. These integrations can have wide-ranging effects, such as unlocking a door from an intercom or tracking access events alongside surveillance footage.
Hardware and software working together
As we’ve seen, modern commercial building access control systems are far more than electronic versions of door locks. Through the combination of professional hardware and configured software, these systems are tightly integrated in both the physical infrastructure and needs of your organization in order to secure your physical assets. As an experienced integrator, ESI Technologies helps align both software and hardware choices to form the foundation of your operational security.
This is part of a larger guide where we’ll explore every aspect of access control—from how it works, considerations when choosing solutions for your commercial property, all the way to overlooked benefits it provides. Keep watch for the next post where we’ll look at specific complexities and use cases for commercial buildings!
Do you have questions or concerns about access control solutions for your commercial building or organization? ESI Technologies has decades of experience working with organizations across varied industries to install and maintain access control systems. Contact us today for help finding solutions that fit your access control needs!

